
In this article we will explore one type of smart lock, however the process for hacking any smart lock is the same so you can take these methods and apply them to any smart lock you like. The idea of the August Smart Lock is that it can be remotely locked and unlocked using a mobile device. This become problematic because software can always be hacked and as you will see we hacked this one.
The August Smart Lock works with both iOS and Android operating systems. Furthermore, the lock allows an individual to give a temporary authorization to a different phone in order for them to control the locking and unlocking of this device. The functionality also permits one to grant permanent access to another phone with the software installed. Alas, the fatal flaw of a system that is not close looped. Let’s now learn how to hack a smart lock.
This digital lock in particular attaches to existing deadbolt style locks. The August replaces the thumb latch on the inside of the deadbolt lock. These locks make a lot of sense for any home owner as it requires very little upfront installment skill and definitely makes your deadbolt more secure with it than without it. Although it may make your home more safe to the common lock picker, it does not protect you from the tech savvy picker that may be lurking.
The August Smart Lock security features were put to the test and the results are not so hot. This lock has a whole host of vulnerabilities which make it highly susceptible to being hacked. The fatal flaw is the functionality that allows one to add other authorized un-lockers. What has been found is that a hacker can easily add themselves as a guest to any lock that happens to be near by.
How We Hacked A Smart Lock
To start with, make backups of the app in random states. This is to say, different random configurations and stages of use including app states and user settings.
Operating System: Android
Backup Tool: Use Chris John Riley’s ‘ab_unpacker.py’ backup script
We are going to make these four different application back ups to start with:
1. When App is first installed
2. When lock has been purveyed by the App
3. After many lock & unlock Commands have been issued
4. After additional users have been added to test lock
Now, take a look at the files stored locally. This reveals that the config data is encrypted, but not so fast. There is a big ole log file that contains highly sensitive data. After analyzing the source code, you can see that the code shows the encryption key that is hard coded in for all local data:
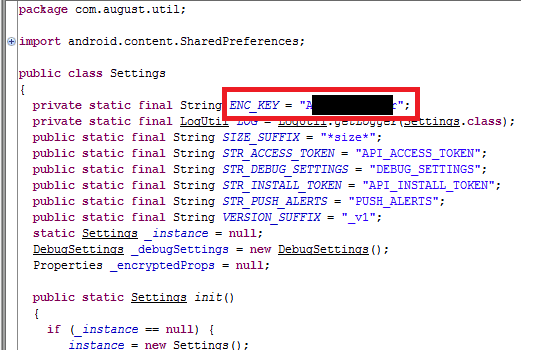

This shows the encryption key hard coded in the source file
Now that we can see what is going on with the encryption, let’s take a slightly closer look. After looking at it for a while, you can see that the routine of this encryption key dictates the cipher being used is AES and ECB. That information was then used to un-encrypt all contents located on the local host file assortment. The files accessed here have the lock UUID, username, phone number and more key identification markers. This data is also accessible in the log file first created by the application before even looking into the cript key.
Cracking The API
Now that we have a solid grasp on the app in general and how it functions on the backend, we move to the API. The goal here is to look out for all the digital communication that the app has with the servers owned by August Smart Locks. The app itself uses a security cert so we can’t just easily take a quick look at it. For this, we have to:
1. De-compile The Entire August App To .smali
2. Remove Certificate Code For Validation
3. Recompile The Entire August App
4. Sign Security Cert
5. Re-Install Application In The Newly Moded Form
Most of the end parts of the August API didn’t allow us to find anything too significant – there was one that did not validate that the user pressing lock/unlock are actually the owner of the lock. Behold, this is the vulnerability that we need to hack an August Smart Lock. This API endpoint that is weak and vulnerable is the one that allows the owner of the August to add a guest to the lock. In finding this, it means that any hacker can create an API request to add their user as a guest to any lock near by with the correct UUID of the lock which can easily be found in the plain text log file that we found up above.
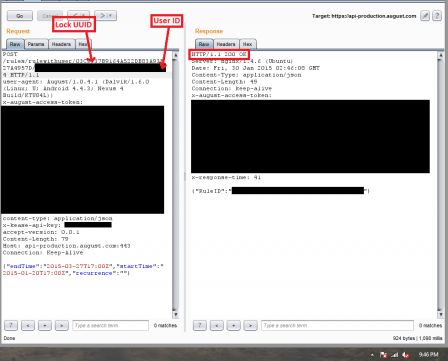

Screenshot of the API call to add guest
Now that the August Smart Lock has been hacked, let’s review the conditions in which need to be present in order to crack this digital lock. For the hacker to crack this lock there are two things needed: UUID of the lock, UID of hacker. The UID can be found using a few different methods:
Method 1: Un-encrypt local storage on hackers mobile phone
Method 2: Intercept API call on hacker’s mobile phone
Method 3: Inspect the local plain text log file that we found earlier
The UUID of an August Smart Lock can be found by simply walking up to one and using the app to scan for August locks that are nearby. The mobile phone will find all that are in range. Once it does, the app will write the UUID of the locks that were discovered in the plain text log file on the mobile phone. Now that you have the UUID of the lock, you can add yourself as a guest using the Moded App that we created above and unlock the door immediately.
Future Considerations
That’s how you hack a smart lock! Keep in mind that this methodology will work for any smart lock. However you may need to make minor adjustments to exploit the specific vulnerabilities in each different make, model and OS that the phone is using. August has reportedly fixed this specific API issue. Plenty more work that can be done using the same methods here to find additional vulnerabilities in these digital locks.
Try backing up the app in even more configurations and settings and states of use in order to find more holes in the security of this lock. If you find any new ones, please let us know! We would be more than happy to include them in our article here. Remember, if a lock as software attached to it, it can and will be hacked. Happy picking!
References: Paul Lariviere & Stephen Hall





![How To Pick A Lock [Fast] – 2020 Complete Guide](https://pickeroflocks.com/wp-content/uploads/thumbs_dir/PICKER-OF-LOCKS-FEATURE-IMAGE-TYPES-OF-LOCKS-6d9vngvzam1muapx27v3bzhmtmfgpkqqan5qhjj1nwq.png)


